In this blog, we will dive into the details of PCI DSS and how it applies to organizations using Azure. This blog will also provide insights on how to design your environment to be PCI DSS compliant.
Introduction
The Payment Card Industry Data Security Standard (PCI DSS) is a set of security standards designed to ensure that all companies that accept, process, store or transmit credit card information maintain a secure environment. PCI DSS applies to all organizations that accept, process, store, or transmit cardholder data, regardless of size or the number of transactions. The standard was developed by major credit card brands, including Visa, Mastercard, American Express, Discover, and JCB, to ensure that merchants follow a set of security guidelines when accepting card payments. Non-compliance can result in hefty fines and damage to a company’s reputation.

For organizations using Microsoft Azure, the good news is that the platform offers a number of features that can help with PCI DSS compliance. However, it’s important to understand the requirements of PCI DSS so you can act on your design considerations and decisions to become compliant with it. By the end of this blog, you will have a better understanding of the importance of PCI DSS compliance and how to achieve it in Azure. Whether you’re a security professional or simply someone looking for knowledge you need to make informed decisions on how to secure data, configure networks, and implement access controls, among other critical security measures. So, let’s get started!
Understanding the Payment Card Industry Data Security Standard
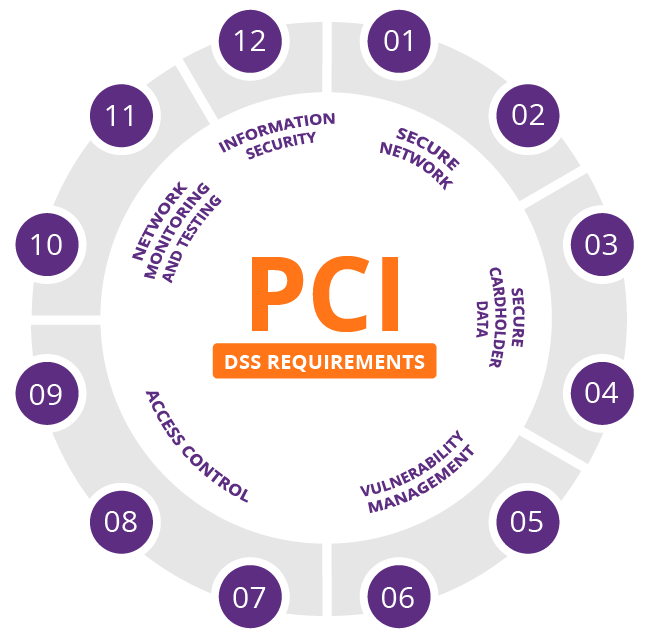
The Payment Card Industry Data Security Standard (PCI DSS) consists of 12 high-level requirements, which are divided into six objectives:
- Build and Protect a Secure Network
- Protect Cardholder Data
- Create a Vulnerability Management Program
- Apply Strong Access Control Measures
- Regularly Monitor and Test Networks
- Create a Policy Regarding Information Security
It’s important to note that the specifics of each requirement and how they are implemented may vary based on the size and type of an organisation. PCI DSS provides a flexible framework for ensuring PCI DSS, but it’s up to you as a professional to determine the best way to meet the requirements in their specific context.
Build and Protect a Secure Network
This category covers requirements for securing the network infrastructure that processes cardholder data, including firewalls, routers, and other network devices. The requirements in this category are:
- Install and maintain a firewall to protect your cardholder data.
- Create and implement standards for configuration of firewalls and routers.
- Create a firewall and router configuration that restrics connections between untrusted networks and all system components in the cardholder data environment.
- Restrict direct global access to any syustem component of the cardholder data medium over the internet.
- Install personal firewall software on all mobile devices that are connected to the internet and used to access the network when they are out of the network.
- Make sure that security policies and operational procedures for managing firewalls are documented, in use, and known to all affected parties.
- Do not use the vendor’s default settings for system passwords and other security parameters.
- Always change the default settings and values provided by the manufacturer and remove or disable unnecessary default accounts before installing any system on the network.
- Create configuration standards for all components of the system.
- Encrypt all non-console administrative access to devices using strong encryption.
- Keep an inventory of all PCI DSS in-scope system components.
- Make sure that security policies and operational procedures are documented, in use, and known to all affected parties to manage the manufacturer’s default values and other safety parameters.
- Shared hosting service providers must protect the environment and cardholder data hosted by each organization.
Protect Cardholder Data
This category covers requirements for protecting sensitive cardholder data, such as encryption and secure storage. The requirements in this category are:
- Protect stored cardholder data.
- Keep cardholder data storage to a minimum by developing and implementing policies, procedures and processes for data retention and destruction of cardholder data (CHD).
- Do not store sensitive authentication data after authorization, even if it is encrypted.
- If the primary account number (PAN) has to be displayed, mask it to view it.
- Make the primary account number unreadable wherever it is stored.
- Create and implement procedures to protect the keys used to protect stored cardholder data from disclosure and misuse.
- Document and implement all key management processes and encryption key procedures used to encrypt cardholder data.
- Security policies and operational procedures must be documented, used and known to all affected parties to protect stored cardholder data.
- Encrypt cardholder data when transmitting over open, public networks.
- Use strong encryption and security protocols to protect sensitive cardholder data during transmission over open, public networks.
- Never send Primary Account Number (PAN) information without password over end-user messaging technologies.
- To encrypt the transmission of cardholder data, ensure that security policies and operational procedures are documented, in use, and known to all affected parties.
Create a Vulnerability Management Program
This category covers requirements for identifying, evaluating, and mitigating security risks and vulnerabilities in the cardholder data environment. The requirements in this category are:
- Protect all systems against malware and update anti-virus software regularly.
- Install anti-virus software on all systems that are commonly affected by malware.
- Make sure all anti-virus mechanisms are working properly.
- Anti-virus software should work effectively and cannot be disabled by users.
- Ensure that security policies and operational procedures are documented, in use, and known to all affected parties to protect systems against malware.
- Develop secure systems and applications.
- Identify vulnerabilities using reputable external sources and create a risk ranking for newly discovered vulnerabilities.
- Install valid security patches provided by the vendor to ensure that all system components and software are protected from known vulnerabilities.
- Securely develop all software applications.
- Create change control processes and follow procedures for all changes in system components.
- Identify and fix common vulnerabilities in software development processes.
- Continuously monitor new threats and vulnerabilities for open web applications and ensure that these applications are protected against known attacks.
- Ensure that security policies and operational procedures are documented, in use, and known to all affected parties to develop secure systems and applications.
Apply Strong Access Control Measures
This category covers requirements for controlling access to cardholder data, including user authentication and authorization. The requirements in this category are:
- Restrict access to cardholder data based on business requirements.
- Limit access to system components and cardholder data only to those who need it for their job functions.
- Create secure access control systems.
- Ensure that security policies and operational procedures to restrict access to cardholder data are documented, in use, and known to all affected parties.
- Identify and authenticate access to system components.
- Define and implement policies and procedures to ensure correct user identity management for users and administrators across all system components.
- Provide appropriate user authentication management for users and administrators in all system components.
- Secure all individual administrative access to the CDE and all remote access to the CDE using multi-factor authentication.
- Document and communicate authentication policies and procedures to all users.
- Do not use group, shared or public IDs, passwords or other authentication methods.
- Where other authentication mechanisms are used, the use of these mechanisms should be assigned as follows.
- Limit all access to any database containing cardholder data.
- Ensure that security policies and operational procedures for authentication and identification are documented, in use, and known to all affected parties.
- Restrict physical access to cardholder data.
- Create and use appropriate facility access controls to limit and monitor physical access to systems in the cardholder data environment.
- Develop procedures to distinguish between staff and visitors easily.
- Restrict physical access to sensitive areas for employees as follows.
- Follow procedures to identify and empower visitors.
- Protect all media that contains physically sensitive data.
- Have strict control over the internal or external distribution and transmission of any media.
- Have strict control over media storage and accessibility.
- Destroy media when it is no longer needed for business or legal reasons.
- Protect devices that receive payment card data through physical interaction from tampering and replacement.
- Ensure that security policies and operational procedures to restrict physical access to cardholder data are documented, in use, and known to all affected parties.
Regularly Monitor and Test Networks
This category covers requirements for monitoring and testing the security of the cardholder data environment, including logging and analysis of security events. The requirements in this category are:
- Track and monitor all access to network resources and cardholder data.
- Create a process that connects access to system components to each user.
- Set up an automatic log review mechanism to reproduce events.
- Record at least the user ID, event type, date and time, success or failure indicator, the origin of the event, and the identity or name of the affected data, resource or system component for evPCI DSS
- Synchronize all critical system clocks and times using time synchronization technology.
- Keep the logs in a way that cannot be altered.
- Regularly review logs and security events for all system components to identify abnormalities or suspicious activity.
- Retain the log history for at least one year and have at least three months of data ready for analysis.
- Create and implement processes for timely detection and reporting of failures of critical security control systems for service providers.
- Ensure that security policies and operational procedures are documented, in use, and known to all affected parties to monitor all access to network resources and cardholder data.
- Test security systems and processes regularly.
- Create processes to test the presence of wireless access points (802.11), and identify all authorized and unauthorized wireless access points quarterly.
- Perform internal and external network vulnerability scans at least every three months and after a significant change in the network.
- Apply a methodology for penetration testing.
- Use intrusion detection or intrusion prevention techniques to detect or prevent network intrusion.
- Set up a change detection mechanism to detect unauthorized modification of critical system files, configuration files or content files.
- Ensure that security policies and operational procedures for security monitoring and testing are documented, in use, and known to all affected parties.
Create a Policy Regarding Information Security
This category covers requirements for establishing, maintaining, and disseminating a formal information security policy that governs the protection of cardholder data. The requirements in this category are:
- Create a policy that addresses information security for all staff.
- Create and publish an information security policy.
- Create and implement a risk assessment process.
- Acceptable usage policies for critical technologies should be developed, and the appropriate use of these technologies should be defined.
- Ensure that security policy and procedures clearly define information security responsibilities for all personnel.
- Assign information security management responsibilities to a person or team.
- Implement a formal information security awareness program to inform all staff about the importance of cardholder data security.
- To minimize the risk of attack from local sources, run a history scan of candidates before hiring.
- Create and implement policies and procedures to manage service providers where cardholder data is shared, or that may affect the security of cardholder data.
- Service providers must notify their customers in writing that they are responsible for the security of the cardholder data they store, process or transmit on behalf of the customer.
- Create and implement an incident response plan. Be prepared to respond immediately to violations.
- Service providers should evaluate at least quarterly to verify that personnel are following security policies and operational procedures.
For detailed information, you can refer to the PCI DSS Quick Reference Guide or the PCI DSS Standard from the PCI SSC Documentation library.
Designing for PCI DSS Compliant Azure Solutions
Within Azure (or any other public cloud) you have to deal with the shared responsibility model and a demarcation between (security) tasks that are performed by the cloud provider and which tasks are performed by your organization. The workload responsibilities vary depending on whether the workload is hosted on Platform as a Service (PaaS) or Infrastructure as a Service (IaaS). That also has an impact on the PCI DSS requirements, and whether it is assigned to Azure or you, or whether responsibility is shared.
Below is explained which responsibilities should be fulfilled by you in the context of implementing PCI DSS compliance in Azure. To implement the PCI DSS in Microsoft Azure, organizations should focus on the following categories:
- Network design: Organizations should design their Azure network to be secure and segmented, with appropriate access controls in place.
- Data protection: Organizations should use Azure features such as Azure Key Vault, Azure Disk Encryption, and Azure Storage Service Encryption to protect sensitive cardholder data.
- Access control: Organizations should use Azure features such as Azure Active Directory and Azure Multi-Factor Authentication to control access to sensitive data and resources.
- Monitoring and logging: Organizations should use Azure features such as Azure Monitor, Azure Log Analytics, and Azure Security Center to monitor and log activity in their Azure environment.
- Incident response: Organizations should have a plan in place for responding to security incidents, and use Azure Security Center to help identify and respond to incidents.
- Compliance: Organizations should use Azure Policy and Azure Security Center to ensure that their Azure environment is compliant with relevant regulations, including PCI DSS.
Network design
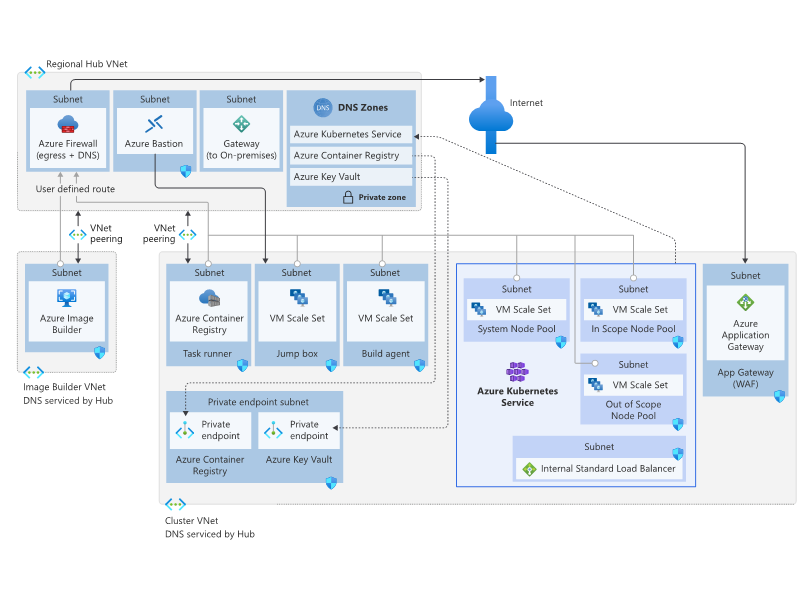
To be compliant with the Payment Card Industry Data Security Standard (PCI DSS) in an Azure environment, there are several network design requirements that must be implemented. These requirements can be achieved by including, but are not limited to, by implementing:
- Segmentation: It is important to segment the cardholder data environment from the rest of the network to reduce the scope of the PCI DSS assessment. This can be achieved using Virtual Networks (VNets) in Azure. A reference architecture of an AKS regulated cluster for PCI-DSS can be found on the Microsoft Architecture Center and used as an example. There is a lot more information in the Microsoft Learn documentation about network-level segmentation, that can help you design a secure and segmented network design.
- Firewall Configuration: Firewalls should be configured to block all incoming and outgoing traffic that is not explicitly required. This helps to protect against unauthorized access to the cardholder data environment. There are various firewall and NVA options within Azure, like Azure Firewall and third-party options. Microsoft has extensive documentation available to get you started with Azure Firewall.
- Network Access Controls: Network access controls should be implemented to prevent unauthorized access to the cardholder data environment. On a networking level, this can be achieved using Network Security Groups (NSGs) in Azure and reinforced with the Access Controls on identity level. In addition, ny administrative access points, such as a jump box, should deny all access in the initial configuration. This also implies the use of Just-in-Time (JIT) access.
- Remote Access: In addition to the above, all remote access must be explicitly allowed. This also means providing access for specific locations and, and where possible, conditional based access needs to be implemented. Remote access to the cardholder data environment should be limited and secured using technologies such as Virtual Private Networks (VPN) and Multi-Factor Authentication (MFA).
- Encryption: All cardholder data transmitted over public networks should be encrypted using strong cryptography and security protocols (for example, TLS, IPSEC, SSH, etc.) to safeguard sensitive cardholder data. Microsoft has written an article on designing your strategical chain of TLS termination points on Microsoft Learn.
Data Protection
To be compliant with the Payment Card Industry Data Security Standard (PCI DSS) in an Azure environment, there are several data protection requirements that must be implemented. These requirements can be achieved by including, but are not limited to, by implementing:
- Data Encryption: All cardholder data should be encrypted both in transit and at rest. Azure provides encryption services such as Azure Disk Encryption, Azure Key Vault, and Azure Storage Service Encryption to help with this.
- Phyiscal Protection: The physical security of the cardholder data environment must be maintained to prevent unauthorized access, theft, or damage. This includes the security of the Azure datacenters, which is obviously the responsibility of Microsoft. You can find all the documentation and evidence/assurance of Microsoft for PCI compliance in their Service Trust Portal.
Access Control
To be compliant with the Payment Card Industry Data Security Standard (PCI DSS) in an Azure environment, there are several access control requirements that must be implemented. These requirements can be achieved by including, but are not limited to, by implementing:
- User Management: Only authorized individuals should have access to the cardholder data environment. Azure provides role-based access control (RBAC) and Azure Active Directory (AD) to support this requirement.
- Authentication: Strong authentication mechanisms, such as Multi-Factor Authentication (MFA), must be used to verify the identity of individuals accessing the cardholder data environment. Azure provides MFA solutions such as Azure AD MFA to support this requirement.
- Authorization: Authorization rules must be established to control access to the cardholder data environment and the information contained within it. This can be achieved using Azure RBAC and AD.
- Password Management: Strong password policies must be in place, including requirements for password complexity, expiration, and history. Azure provides password management solutions such as Azure AD Password Protection to support this requirement.
- Least Privilege: The principle of least privilege must be followed, ensuring that individuals have only the access they need to perform their job responsibilities. This can be achieved using Azure RBAC.
Monitoring and Logging
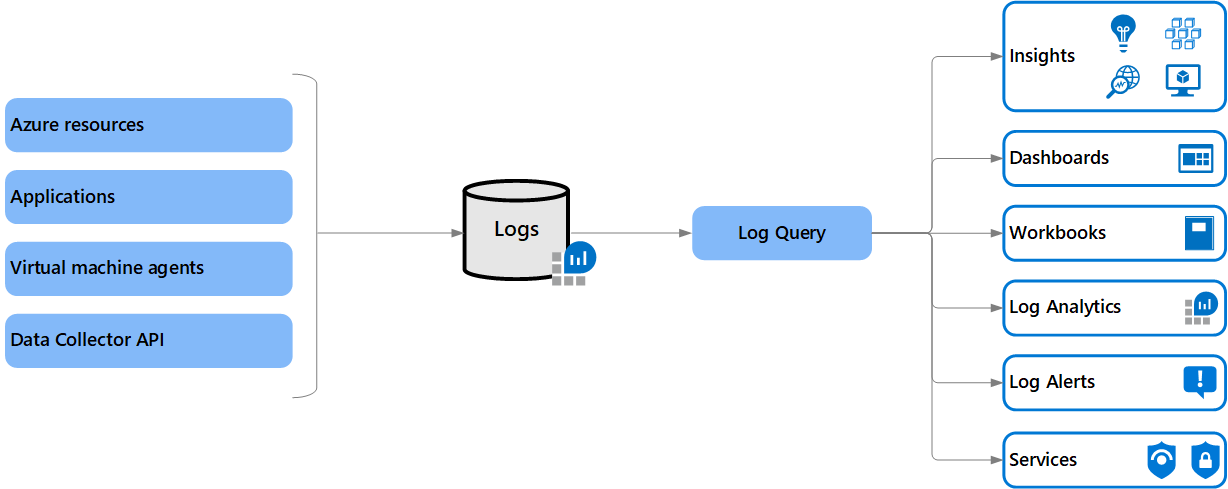
To be compliant with the Payment Card Industry Data Security Standard (PCI DSS) in an Azure environment, there are several monitoring and logging requirements that must be implemented. These requirements can be achieved by including, but are not limited to, by implementing:
- Security Incidents: Monitoring and logging should be in place to detect and respond to security incidents. Azure provides services such as Microsoft Sentinel, Azure Monitor and Azure Log Analytics to support these activities.
- Access Logging: Detailed logs of all access to the cardholder data environment must be maintained, and a mechanism for detecting unauthorized access must be in place. Azure provides services such as Azure Monitor and Azure Log Analytics to support these activities.
- Vulnerabilities: Regular vulnerability scans and penetration testing must be performed to identify and remediate security weaknesses. Azure provides Microsoft Defender services to support these activities.
- Logging Retention: Logs must be retained for at least one year, and longer if required by law or regulation. Azure provides storage solutions such as Azure Blob Storage and Azure Archive Storage to support these requirements, or moving to an Archive Log Analytics Tier to reduce costs in comparison to Basic Log Analytics. You can read more about it in this article by Matthew Lowe.
- Tampering Protection: Logs must be protected from unauthorized modification or deletion. Azure provides tamper-proof storage solutions such as Azure Blob Storage and Azure Archive Storage to support these requirements.
Incident Response
To be compliant with the Payment Card Industry Data Security Standard (PCI DSS) in an Azure environment, there are several incident response requirements that must be implemented. These requirements can be achieved by including, but are not limited to, by implementing:
- Response Planning: A formal incident response plan must be in place and tested regularly to ensure that the organization can respond quickly and effectively in the event of a security breach. This plan should include steps for identifying, containing, and resolving security incidents, as well as steps for communicating with stakeholders.
- Alerting: Alerts must be configured to notify the appropriate personnel in the event of a security incident. Azure provides services such as Azure Alerts to support these activities.
- Communication: As part of your formal incident response plan, a mechanism for rapid communication with stakeholders, including law enforcement, must be in place to ensure that incidents are reported and resolved in a timely manner. Azure provides solutions such as Azure Notification Hubs and Azure Functions to support these requirements.
- Lessons Learned: A process must be in place to document lessons learned from security incidents and to incorporate these lessons into future incident response plans. Azure provides solutions such as Azure DevOps and Azure Boards to support these requirements, which is a great solution to support these requirements.
Compliance
To be compliant with the Payment Card Industry Data Security Standard (PCI DSS) in an Azure environment, there are several compliance requirements that must be implemented. These requirements can be achieved by including, but are not limited to, by implementing:
- Documentation: Detailed documentation of the cardholder data environment and associated security controls must be maintained. This documentation should include information on the architecture, network topology, and security policies and procedures. Azure provides solutions such as Azure Policy and Azure Resource Manager templates to support these requirements.
- Patch Management: Regular patch management should be in place to ensure that the operating systems and applications used in the cardholder data environment are up-to-date and free of vulnerabilities.
- Assessments and Reviews: Regular assessments must be performed to verify that security controls are in place and are functioning as intended. Azure provides services such as Microsoft Defender for Cloud and Azure Compliance Manager to support these activities.
- Reporting: Regular reporting on the compliance status of the cardholder data environment must be provided to stakeholders. Azure provides services such as Azure Compliance Manager and Power BI to support these requirements.
These are most of the key requirements for PCI DSS compliant compliance in an Azure environment. It’s important to note that compliance with PCI DSS involves multiple control objectives and requirements beyond just compliance. Ultimately, the applicability and fulfillment of each requirement partly depends on the chosen technologies and service types (for example, between PaaS and IaaS).
Closing words
Becoming PCI DSS compliant in Azure requires careful planning, implementation, and monitoring of your Azure environment. Azure provides a range of features and tools to help you meet the requirements of PCI DSS and protect sensitive cardholder data. The key to a successful implementation is to understand the requirements of PCI DSS and how to use Azure to meet them. This blog has provided an overview of the requirements, as well as guidance on how to design your environment to be PCI DSS compliant using Azure features such as Azure Key Vault, Azure Disk Encryption, Azure Storage Service Encryption, Azure Active Directory, Azure Multi-Factor Authentication, Azure Monitor, Azure Log Analytics, Azure Security Center, and Azure Policy. To learn more about PCI DSS compliance in Azure, refer to the links provided to Microsoft’s documentation or check out some of the resources below to help you forward:
- PCI DSS Requirements
- Service Trust Portal - PCI DSS
- New PCI DSS Azure Blueprint makes compliance simpler
- Azure Security and Compliance Blueprint for PCI DSS-compliant Payment Processing environments
With a well-planned and implemented PCI DSS compliant solution in Azure, you can ensure the protection of sensitive cardholder data and minimize the risk of a data breach.
Thank you for taking the time to go through this post and making it to the end. Stay tuned because we’ll keep continuing providing more content on topics like these in the future.

