In this blog, we discover how to enhance Azure governance with Azure Governance Visualizer. We’ll explore its powerful features for automating insights into Azure management group hierarchy, Azure Policy, RBAC settings, and security best practices.
What is Azure Governance Visualizer?
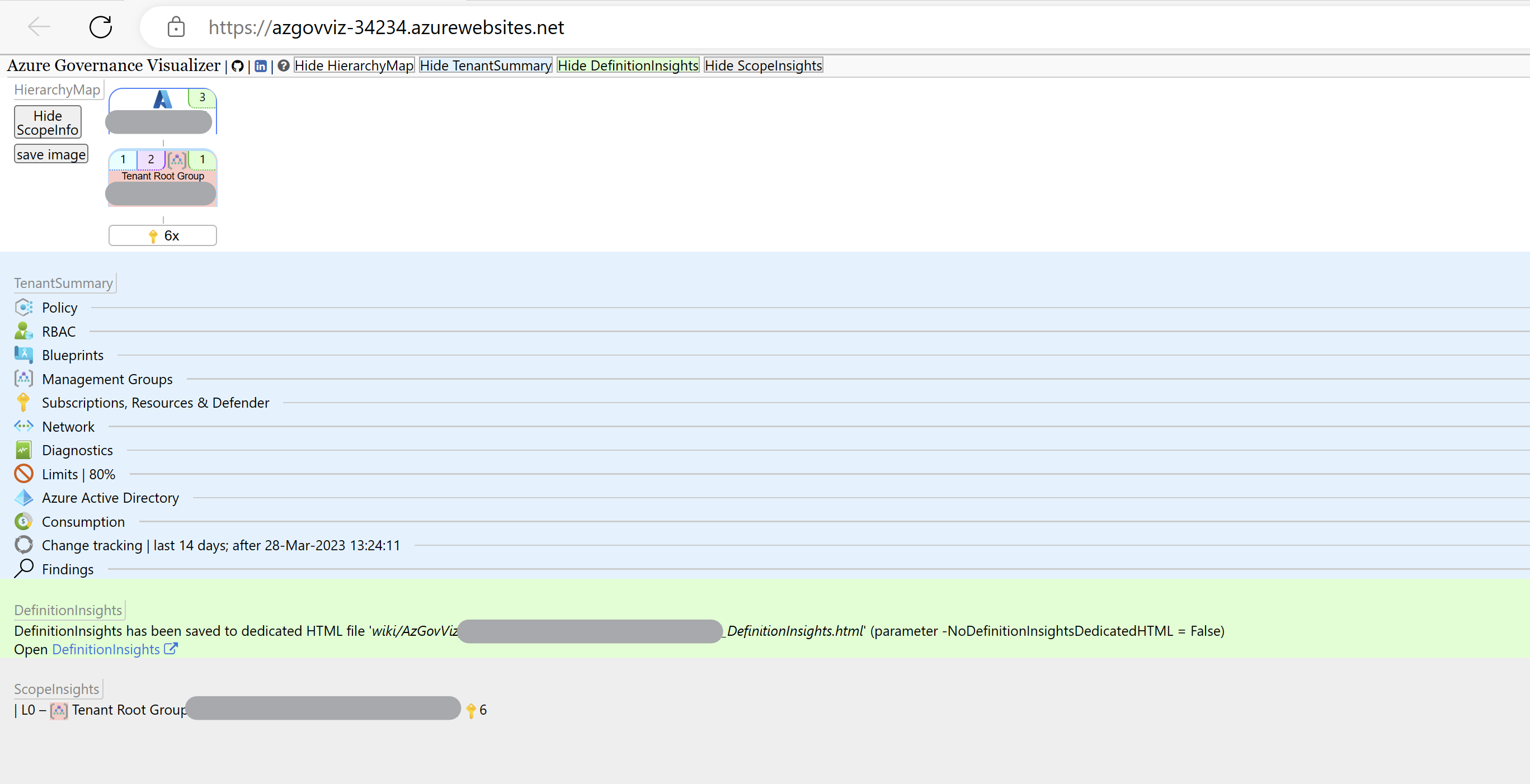
Azure Governance Visualizer is a PowerShell-based tool designed to help you give insights into the governance structure and policies of your Azure tenants. Rather than manually navigating through the complexities of Azure’s management group hierarchy and governance settings, this tool automates the process, providing you with detailed reports and analyses.
The tool operates by traversing through the management group hierarchy of an Azure tenant down to the subscription level. Along the way, it captures crucial governance-related data, including information regarding Azure Policy, role-based access control (RBAC), Blueprints, and more. This collected data is then used to generate various types of insights and reports, enhancing the visibility and understanding of an organization’s Azure governance landscape.
Azure Governance Visualizer (AzGovViz) includes several key features and functionalities, like:
- Hierarchy Mapping: AzGovViz creates a visual representation of the management group hierarchy, offering a clear overview of how resources are structured within the Azure environment.
- Policy Insights: AzGovViz captures details related to Azure Policy, including custom policy definitions, orphaned policy definitions, and policy assignments. This allows you to ensure compliance with regulatory requirements and internal policies.
- RBAC Analysis: AzGovViz provides insights into role-based access control settings, including custom role definitions, orphaned role definitions, and role assignments. This helps you manage access permissions effectively and maintain security standards.
- Security and Best Practice Analysis: AzGovViz offers analysis and recommendations based on Azure’s security best practices, helping you identify potential security vulnerabilities and improve overall security posture.
- Microsoft Entra ID Insights: AzGovViz integrates with Microsoft Entra ID for authentication, ensuring secure access to the generated reports and insights.
AzGovViz can be automated and integrated into existing CI/CD pipelines using services like Azure Pipelines or GitHub Actions. This automation streamlines the process of running the visualizer and generating reports, allowing you to stay up-to-date with their Azure governance status effortlessly.
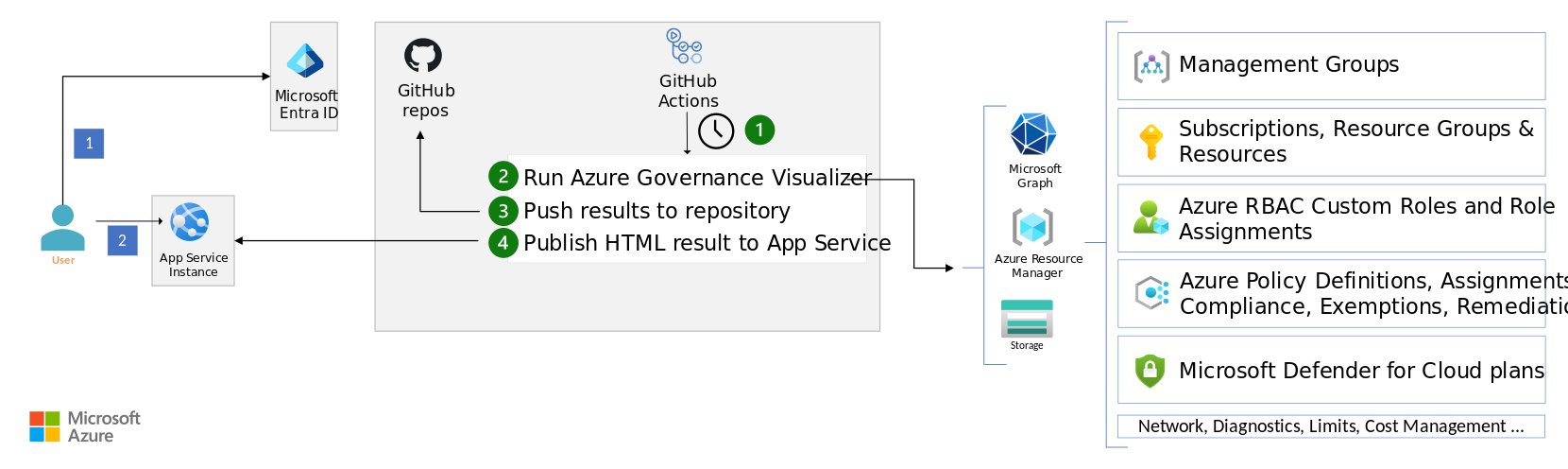
Azure Governance Visualizer generates reports in HTML, MD, and CSV formats, providing flexibility in how the insights are consumed and shared within your organization. These reports can be securely hosted on Azure App Service, making them easily accessible to authorized users.
Security and cost optimization are key considerations in the design and implementation of Azure Governance Visualizer. AzGovViz ensures that access to sensitive governance data is restricted to authorized individuals through authentication mechanisms like Microsoft Entra ID. Additionally, measures such as IP restrictions and access logging are implemented to enhance security and compliance.
From a cost optimization perspective, Azure Governance Visualizer leverages lightweight resources like the B1 (Basic) tier of Azure App Service to host the reports, minimizing unnecessary expenses. Operational excellence is also emphasized through monitoring and updating mechanisms to ensure the tool remains efficient and up-to-date with the latest Azure governance features and best practices.
Deploying Azure Governance Visualizer
Prerequisites
Before diving into the deployment process, ensure you have the following prerequisites in place:
- Azure Tenant with Owner Permissions: You need access to an Azure tenant with Owner permissions to create and manage Azure resources, including App Service plans, and other components required for Azure Governance Visualizer. You also need Global Administrator permissions, so you have sufficient permissions to register Azure AD applications and assign appropriate roles to users within the Azure AD tenant.
- Active Azure Subscriptions: You must have one or more active Azure subscriptions where you will deploy the Azure Governance Visualizer resources.
- GitHub Account: A GitHub account is necessary to host the Azure Governance Visualizer codebase and configuration files in a GitHub repository.
- Basic Terraform Knowledge: Familiarity with Terraform is required to deploy Azure Governance Visualizer using infrastructure-as-code principles.
- Visual Studio Code (Optional): While not strictly required, Visual Studio Code is recommended as an integrated development environment (IDE) for editing Terraform configuration files and managing GitHub repositories.
Creating a service principle
In order to run Azure Governance Visualizer, we need to create a service principal (Microsoft Entra ID app registration). We will use the Terraform Azure Active Directory Provider to do so.
Create a new file (e.g. service_principle.tf) and copy the code below. This will create the service principle, and add the following API permissions that are required in order for Azure Governance Visualizer to work:
- Application / Application.Read.All
- Group / Group.Read.All
- User / User.Read.All
- PrivilegedAccess / PrivilegedAccess.Read.AzureResources
data "azuread_client_config" "current" {}
data "azuread_application_published_app_ids" "well_known" {}
data "azuread_service_principals" "all" {
return_all = true
}
data "azuread_service_principal" "msgraph" {
client_id = data.azuread_application_published_app_ids.well_known.result.MicrosoftGraph
}
resource "azuread_application" "azgovviz" {
display_name = "AzureGovernanceVisualizer"
owners = [data.azuread_client_config.current.object_id]
required_resource_access {
resource_app_id = data.azuread_application_published_app_ids.well_known.result.MicrosoftGraph
resource_access {
id = data.azuread_service_principal.msgraph.app_role_ids["Application.Read.All"]
type = "Role"
}
resource_access {
id = data.azuread_service_principal.msgraph.app_role_ids["Group.Read.All"]
type = "Role"
}
resource_access {
id = data.azuread_service_principal.msgraph.app_role_ids["User.Read.All"]
type = "Role"
}
resource_access {
id = data.azuread_service_principal.msgraph.app_role_ids["PrivilegedAccess.Read.AzureResources"]
type = "Role"
}
}
}
resource "azuread_service_principal" "azgovviz" {
client_id = azuread_application.azgovviz.client_id
app_role_assignment_required = false
owners = [data.azuread_client_config.current.object_id]
feature_tags {
enterprise = true
gallery = true
}
}
resource "azuread_app_role_assignment" "azgovviz" {
for_each = { for v in flatten([
for rra in azuread_application.azgovviz.required_resource_access : [
for ra in rra.resource_access : {
resource_object_id = one([
for sp in data.azuread_service_principals.all.service_principals :
sp.object_id
if sp.client_id == rra.resource_app_id
])
app_role_id = ra.id
}
]
]) : join("|", [v.resource_object_id, v.app_role_id]) => v }
principal_object_id = azuread_service_principal.azgovviz.object_id
resource_object_id = each.value.resource_object_id
app_role_id = each.value.app_role_id
}
The configuration also pre-authorizes the service principle with the specified permissions to access the application’s APIs without requiring user consent. Adjust the values to your personal preferences if necessary, and run terraform apply to create the service principle.
Create a new repository from the AzGovViz Accelerator
Next, we’ll create a copy of the Azure Governance Visualizer Accelerator in our own GitHub repository. We will use the Terraform GitHub Provider to do so. If you rather do this manually, please follow GitHub’s official guide on creating a repository from a template.
Create a new file (e.g. gh_repo.tf) and copy the code below. This will create a copy of the Azure Governance Visualizer Accelerator repository. Adjust the values to your personal preferences if necessary, and run terraform apply to create the repository.
resource "github_repository" "azgovviz" {
name = "AzGovViz"
description = "Azure Governance Visualizer"
visibility = "private"
is_template = false
template {
owner = "azure"
repository = "Azure-Governance-Visualizer-Accelerator"
include_all_branches = true
}
}
Once finished, you can check your GitHub repositories to validate the process was executed properly.
Configure federated credentials
We need to configure federated credentials for our service principal to trust tokens issued by GitHub Actions, allowing them to be exchanged for Azure AD tokens through the Azure AD token exchange service. We will use the Terraform Azure Active Directory Provider again for this configuration.
Reopen the earlier created file for the service principal (service_principal.tf) and insert the code below to this file. This will create the needed federated credentials. Adjust the values to your personal preferences if necessary, and run terraform apply after.
resource "azuread_application_federated_identity_credential" "azgovviz" {
application_id = azuread_application.azgovviz.id
display_name = "AzureGovernanceVisualizer_GitHub_Actions"
description = "Azure Governance Visualizer GitHub Actions"
audiences = ["api://AzureADTokenExchange"]
issuer = "https://token.actions.githubusercontent.com"
subject = "repo:<your-organization>/<your-repo-name>>:ref:refs/heads/<your-branch-name>"
}
Grant permissions in Azure
We need to grant ‘Reader’ permissions in Azure for the service principal. Let’s create a ‘Reader’ RBAC role assignment on a target management group scope for the service principal that will run Azure Governance Visualizer. We will use the Terraform Azure Resource Manager Provider for this.
Reopen the file for the service principal (service_principal.tf) again, and insert the code below to this file. This will add the ‘Reader’ role assignment to the service principal. Adjust the values to your personal preferences if necessary, and run terraform apply after.
data "azurerm_client_config" "current" {}
resource "azurerm_role_assignment" "azgovviz" {
scope = "/providers/Microsoft.Management/managementGroups/<your-management-group-id>"
role_definition_name = "Reader"
principal_id = azuread_service_principal.azgovviz.id
}
Create a Microsoft Entra application
Next, we’ll create a Microsoft Entra application for user authentication to the Azure Web App that will host Azure Governance Visualizer. We will use the Terraform Azure Active Directory Provider again for this configuration. Note that we also use the Terraform Random UUI Provider to generate a UUID.
Create a new file (e.g. app_registration.tf) and copy the code below. This will create the Application Registration for the WebApp, enable ID tokens to allow OpenID Connect user sign-ins from the App Service on the specific scope. Adjust the values to your personal preferences if necessary, and run terraform apply after.
resource "random_uuid" "azgovviz" {}
resource "azuread_application_registration" "azgovviz" {
display_name = "<webapp-name>"
description = "My AzGovViz application"
sign_in_audience = "AzureADMyOrg"
implicit_id_token_issuance_enabled = true
}
resource "azuread_application_redirect_uris" "azgovviz" {
application_id = azuread_application_registration.azgovviz.id
type = "Web"
redirect_uris = [
"https://<webapp-name>.azurewebsites.net/.auth/login/aad/callback",
]
}
resource "azuread_application_permission_scope" "azgovviz" {
application_id = azuread_application_registration.azgovviz.id
scope_id = random_uuid.azgovviz.id
value = "user_impersonation"
admin_consent_description = "AzGovViz Web App Azure AD authentication"
admin_consent_display_name = "Azure Governance Visualizer"
user_consent_description = "AzGovViz Web App Azure AD authentication"
user_consent_display_name = "Azure Governance Visualizer"
}
Create a resource group and grant permissions
It is time to create a resource group, and assign our service principal the ‘Website Contributor’ and ‘Web Plan Contributor’ roles to this resource group. We will again use the Terraform Azure Resource Manager Provider for this.
Create a new file (e.g. main.tf) and copy the code below. This will create a resource group and grant our service principal the appropriate roles to the resource group. Adjust the values to your personal preferences if necessary, and run terraform apply to create the repository.
resource "azurerm_resource_group" "azgovviz" {
name = "<resource-group-name>"
location = "<resource-group-location>"
}
resource "azurerm_role_assignment" "azgovviz-website" {
scope = azurerm_resource_group.azgovviz.id
role_definition_name = "Website Contributor"
principal_id = azuread_service_principal.azgovviz.id
}
resource "azurerm_role_assignment" "azgovviz-webplan" {
scope = azurerm_resource_group.azgovviz.id
role_definition_name = "Web Plan Contributor"
principal_id = azuread_service_principal.azgovviz.id
}
Create the GitHub secrets, variables, and permissions
To make the GitHub Action workflow we copied from the Azure Governance Visualizer Accelerator template work, we need to define a few secrets, variables and permissions. We will use the Terraform GitHub Provider to do so.
| Secret | Value |
|---|---|
| CLIENT_ID | Application ID of the identity that will run Azure Governance Visualizer |
| ENTRA_CLIENT_ID | Application ID of the identity that will configure user authentication to the Azure Web App |
| ENTRA_CLIENT_SECRET | Secret of the identity that will be used to configure user authentication to the Azure Web App |
| SUBSCRIPTION_ID | Azure subscription ID |
| TENANT_ID | Microsoft Entra tenant ID |
| MANAGEMENT_GROUP_ID | Azure management group ID |
| Variable | Value |
|---|---|
| RESOURCE_GROUP_NAME | Name of the pre-created resource group to host the Azure Web App |
| WEB_APP_NAME | Globally unique name of the Azure Web App |
Reopen the file for the GitHub repository (gh_repo.tf) again, and insert the code below to this file. This will add the secrets, variables, and permissions mentioned above. Adjust the values to your personal preferences if necessary, and run terraform apply after.
resource "github_actions_secret" "client_id" {
repository = github_repository.azgovviz.name
secret_name = "CLIENT_ID"
encrypted_value = "<your-client-id>"
}
resource "github_actions_secret" "entra_client_id" {
repository = github_repository.azgovviz.name
secret_name = "ENTRA_CLIENT_ID"
encrypted_value = "<your-entra-client-id>"
}
resource "github_actions_secret" "entra_client_secret" {
repository = github_repository.azgovviz.name
secret_name = "ENTRA_CLIENT_SECRET"
encrypted_value = "<your-entra-client-secret>"
}
resource "github_actions_secret" "subscription_id" {
repository = github_repository.azgovviz.name
secret_name = "SUBSCRIPTION_ID"
encrypted_value = "<your-subscription-id>"
}
resource "github_actions_secret" "tenant_id" {
repository = github_repository.azgovviz.name
secret_name = "TENANT_ID"
encrypted_value = "<your-tenant-id>"
}
resource "github_actions_secret" "management_group_id" {
repository = github_repository.azgovviz.name
secret_name = "MANAGEMENT_GROUP_ID"
encrypted_value = "<your-management-group-id>"
}
resource "github_actions_variable" "resource_group_name" {
repository = github_repository.azgovviz.name
variable_name = "RESOURCE_GROUP_NAME"
value = "<your-resource-group-name>"
}
resource "github_actions_variable" "web_app_name" {
repository = github_repository.azgovviz.name
variable_name = "WEB_APP_NAME"
value = "<your-web-app-name>"
}
Deploy Azure Governance Visualizer
Finally, it is time to run the GitHub Action workflows to deploy the resources and application. Navigate to the GitHub Actions in your created repository, and run the DeployAzGovVizAccelerator workflow. This will initialize the accelerator, deploy the Azure Web App and configure Microsoft Entra authentication. It will also trigger the workflow to sync the latest AzGovViz code to your repository.
When all is set, run the DeployAzGovViz workflow to deploy AzGovViz and publish it to the Azure Web App. Once the DeployAzGovViz workflow has been ran successfully, navigate to the Azure Web App on the Azure portal and click Browse to access the visualizer. You’ll notice that you’ll need to be authenticated with Microsoft Entra ID.
Closing words
Cloud governance is paramount in today’s digital landscape, where the scale and complexity of cloud environments continue to grow. Proper governance practices not only ensure compliance with regulatory requirements and internal policies but also help in optimizing costs, enhancing security, and maintaining operational excellence. Azure Governance Visualizer serves as a crucial tool for organizations seeking to streamline and optimize their Azure governance practices. With features such as hierarchy mapping, policy insights, RBAC analysis, security and best practice recommendations, and integration with Microsoft Entra ID for secure authentication, Azure Governance Visualizer offers a holistic approach to managing Azure governance.
Furthermore, its ability to be automated and integrated into existing CI/CD pipelines enhances operational efficiency and ensures that organizations can stay up-to-date with their Azure governance status effortlessly. As organizations continue to adopt cloud technologies, the need for robust governance tools like Azure Governance Visualizer becomes increasingly essential. By providing visibility, insights, and actionable recommendations, AzGovViz empowers organizations to effectively manage and govern their Azure environments, ultimately driving success in their cloud journey.
Thank you for taking the time to go through this post and making it to the end. Stay tuned, because we’ll keep continuing providing more content on topics like this in the future.
